Setting up vIDM for NSX-T
- Hammad Alam
- Jun 25, 2019
- 2 min read
Updated: Oct 14, 2022
Angel already has a great blog posted to setup vIDM with NSX-T, so I am not duplicating what is already there. This post is additional things you may have to do to get it working.
This is for vIDM 2.x version but still applies to vIDM 3.x
Step-by-step vIDM install (non NSX-T) https://techzone.vmware.com/resource/reviewers-guide-premises-vmware-identity-manager#section4
Using CA Signed Cert with vIDM
If the vIDM appliance is using a CA signed cert then the step in “Get the VMware Identity Manager appliance certificate thumbprint” needs some update.
Issue the following command
openssl x509 -in vidm.corp.local_cert.pem -noout -sha256 -fingerprintEven if vIDM is not using self-signed cert, the certificate in this location is still the self-signed and is not replaced by the CA signed cert user provided.
To work around this, just create a file in the same location and put the PEM of your CA signed cert that is being used by vIDM and run the command against that file instead.
Fingerprint
The output of the Fingerprint has colons in it whereas the NSX UI wants it without the colons hence user will have to remove it manually.
SHA256
Fingerprint=F1:5F:88:EB:BE:14:60:BE:DA:AB:E7:8E:BF:CC:92:AD:A3:98:E9:A8:48:F8:C8:1B:87:62:E9:56:1D:03:AB:C5
F15F88EBBE1460BEDAABE78EBFCC92ADA398E9A848F8C81B8762E9561D03ABC5Your username or password is incorrect, when logging into NSX-T Manager
Setting up vIDM with NSX Manager. Everything seems to be okay. You can add the domain groups to NSX Roles in NSX Manager. You can login to NSX Manager with the domain cred and it takes the credential but when login, it says the user don't have access as shown below.

This can occur if you choose a Base DN that is not the root of the Domain. Changed Base DN to the root DN as shown below.

Access Denied when login to NSX-T Manager
Setting up vIDM with NSX Manager. Everything seems to be okay. You can add the domain groups to NSX Roles in NSX Manager. You can login to NSX Manager with the domain cred and it takes the credential but when login, it says the user don't have access. (***Did "NOT" have to do this when choosing the root domain for the Base DN shown above***).


To validate this issue, login to the vIDM appliance with the domain credential and you should still get the ACCESS DENIED message.
Workarounds
There could be few things going wrong
1. There are four required “Mapped Attributes” in the user. I did not had lastName and email address fields in AD for my users. This was causing sync issues


2. Safeguard setting was low so bumped that up

3. I only had Groups in the sync as I don’t want to sync individual users. When I added a user, that user worked no problem (after adding lastname and email in AD)
4. For Groups. There is a disturbing thing. Read the description below, which clearly says that users within the Groups will not be synced unless a resource is given to them

5. You can selectively sync a group though. See below where I selectively synced a group and the users showed up.
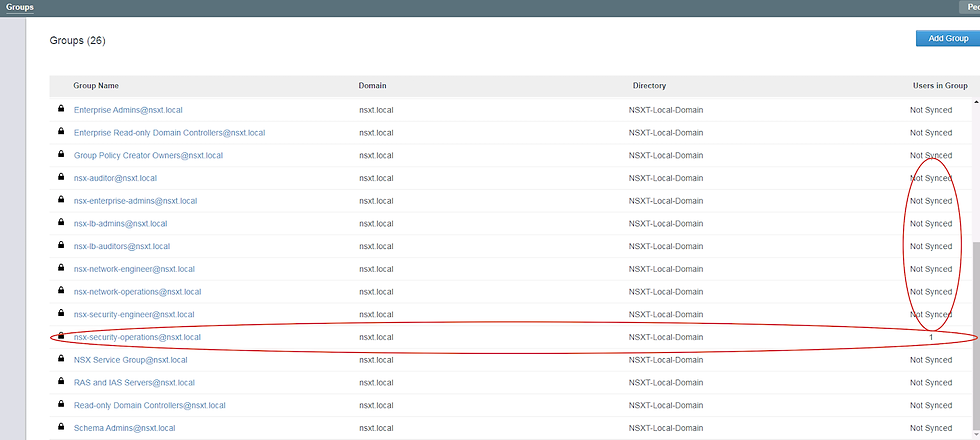
6. Now I am going to manually sync the groups. Once sync users option is selected, the new users in the group are automatically synced.

7. Also, should change the default sync from Weekly to more appropriate value





Comments